The computing scenario has changed a lot over the years, provoking an explosion of new technologies, interaction scenarios and. most importantly, a democratization of technology usage. In the fascinating research area of Systems Security the goal has been always to…
There is very useful technique to know who wants to enter your network and which are his intentions. Simply leave a pot of vulnerabilities in the middle of the woods and wait for the bees to approach. Most times they…
Today we will play with a web vulnerabilities search tool with which we can check very easily the safety of our web applications. The tool in question is Vega, an Open Source platform web auditing can help us identify and…
Making the installation of a new wireless router at home, although at first glance seems simple, something always aindicated by operators, it is not at all. If it is true that to start using it is just connect, look for the wireless…
The movement of Internet of Things ,IOT in the acronym, is becoming increasingly booming. This movement, walking hand in hand with the philosophy Do-It-Yourself (DIY) has led to a proliferation of projects based on open-hardware, using Arduino, BeagleBoard, Raspberry Pi…
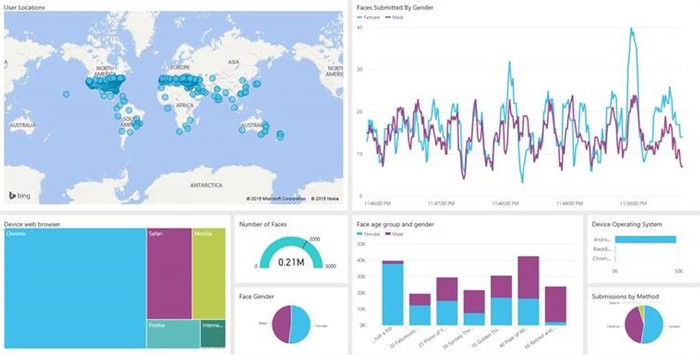
Some time ago we talked about a tool presented by Microsoft which became viral (figures on the success of the tool are quite impressive: 80 million people uploaded 500 million images in less than 7 days.),since it guessed your age (or at least tried it).…